
AEMAUTO-RMIT-Service-Access-Information-Template-v1
Learn how to make a strong password, protect your data and connect to your desktop remotely.
Learn how to make a strong password, protect your data and connect to your desktop remotely.

Learn how to make a strong password, protect your data and connect to your desktop remotely.
Learn how to make a strong password, protect your data and connect to your desktop remotely.
Learn how to make a strong password, protect your data and connect to your desktop remotely.
In order for staff to use Self Service Password Reset (SSPR), you must first set up your phone details in Workday. Visit the My details page to learn more.

Watch this video and learn how to use RMIT's self-service reset tool to change your password.
Go to Self Service Password Reset or select the "Reset your password"/"Forgot your password?" link at any CAS or MyApps login page.
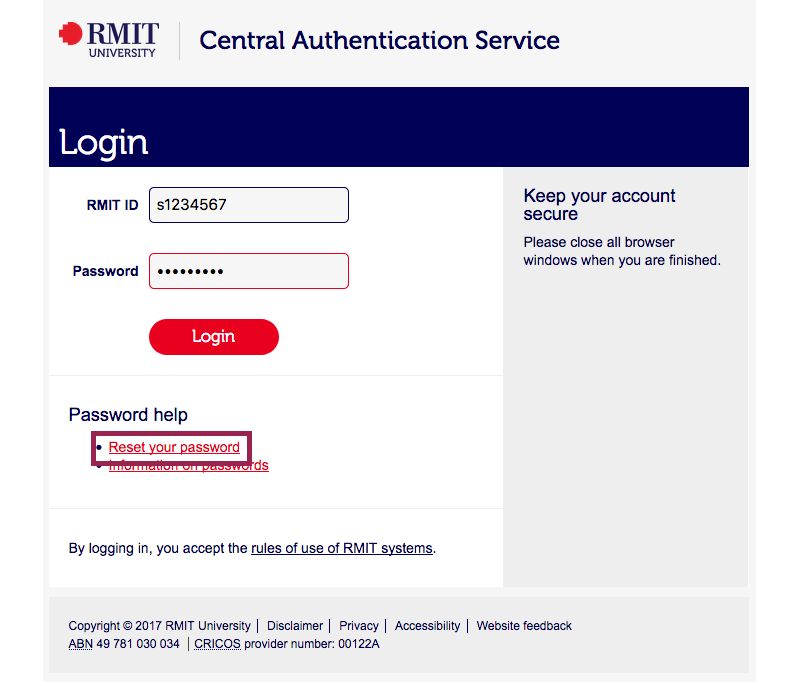
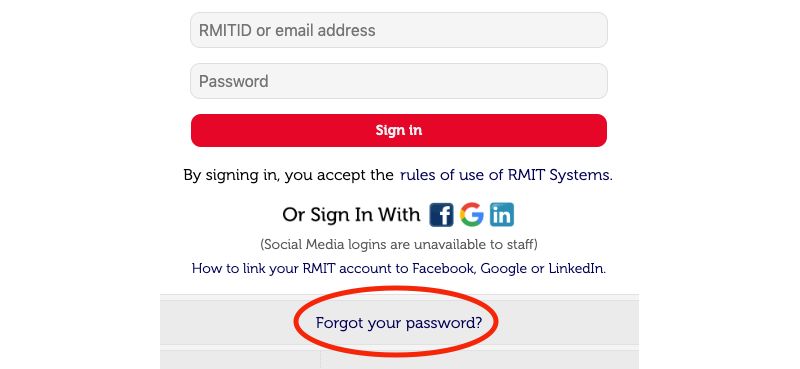
Retrieve the code and enter it into the field (the code is case sensitive).
You can now create a new password for your account.
We have put several password controls rules in place to help you create secure passwords and protect our data.
Minimum password characters: 8 characters
Maximum password characters: 25 characters
Password history: 15 passwords
Minimum password age: 0 days
Maximum password age: 180 days
Password complexity: Password must contain characters from three of the following four categories:
Minimum password characters: 10 characters
Maximum password characters: 25 characters
Password history: 15 passwords
Minimum password age: 0 days
Maximum password age: 90 days
Password complexity: Password must contain characters from three of the following four categories:
Minimum password characters: 20 characters
Maximum password characters: 25 characters
Password history: 15 passwords
Minimum password age: 0 days
Maximum password age: 365 days
Password complexity:
Each day, enormous amounts of data and information are created, stored and distributed across RMIT. Keeping this information and our staff, students and stakeholders safe is a top priority. To ensure our data is protected, new sensitivity labels can now be applied in Office 365 to all emails and documents that you create and/or share at RMIT. The sensitivity label you select will depend on the type of information you are planning to share and how the recipient may use it.
If you receive any email of which you are suspicious, please do not follow any links contained in the email - instead, report the email via the Phish Alert Report icon on your Office Toolbar.
Please ensure you are forwarding the original email to the above address, and not composing a new one.
NOTE: when you use the Phish Alert Report icon, you should receive an automatic reply.
Automatic reply text:
Thank you for taking the time to report your suspected Phishing email. Your action in reporting this email is extremely valuable and helps us to respond quickly to real Phishing attacks against RMIT. For training purposes, RMIT will regularly send simulated Phishing emails to RMIT staff. We encourage you to continue to report all suspected incidents of Phishing.
Next steps:
If your email is identified as genuine Phishing, we will take the necessary steps to minimise any real or potential cyber security breach. We will block the sender and communicate to impacted staff if necessary.
Phishing is an ongoing threat to the online safety of RMIT data.
If in doubt:
Thank you for your efforts in helping to protect RMIT’s data and information.
For urgent Cyber security assistance, please contact: +61 3 9925 8888
Acknowledgement of Country
RMIT University acknowledges the people of the Woi wurrung and Boon wurrung language groups of the eastern Kulin Nation on whose unceded lands we conduct the business of the University. RMIT University respectfully acknowledges their Ancestors and Elders, past and present. RMIT also acknowledges the Traditional Custodians and their Ancestors of the lands and waters across Australia where we conduct our business - Artwork 'Luwaytini' by Mark Cleaver, Palawa.
Acknowledgement of Country
RMIT University acknowledges the people of the Woi wurrung and Boon wurrung language groups of the eastern Kulin Nation on whose unceded lands we conduct the business of the University. RMIT University respectfully acknowledges their Ancestors and Elders, past and present. RMIT also acknowledges the Traditional Custodians and their Ancestors of the lands and waters across Australia where we conduct our business.